How Personality Psychology Is Rewriting the Security-Convenience

Picture this: Two users. Same app. Same security feature. One experiences it as liberation - a frictionless gateway to what they need. The other experiences it as a loss of control - a black box they can't trust.
Tired of reading? We got something for you!
Same technology. Opposite reactions. What changed?
Nothing about the product changed. Everything about the person was different.
What has changed is that the digital authentication sector has reached a critical inflection point. The passwordless authentication market hit $24.1 billion in 2025, with 70% of organizations either implementing or planning to adopt passwordless solutions. Yet even as technology solves the "how" of frictionless security, many companies still struggle with the "why" - why some users embrace biometric login while others cling to their password managers, why a feature that delights one segment alienates another.
The answer isn't in the technology. It's in psychology.
The Paradox That Defined a Generation of UX
Over an extended period, the security-convenience trade-off was treated as gospel. Want better security? Add more authentication factors, longer passwords, and stricter protocols. Need better conversion? Remove friction, simplify flows, make it "one-tap easy."
The result? 31% of consumers have abandoned transactions due to password resets, and 19% have left brands entirely after forgetting credentials. Meanwhile, the "secure" systems we built became so cumbersome that users created insecure workarounds - the infamous Post-it note password diary stuck to the monitor became a symbol of security theater gone wrong.
The data now tells a different story: 68% of data breaches involve human error, and 81% of security incidents stem from breached credentials. The old trade-off wasn't just frustrating - it was fundamentally broken.
This is the major shift: phishing-resistant, passwordless authentication grew by 63% in a single year, rising from 8.6% to 14.0% adoption. Modern passkeys, FIDO2, and device-bound authentication deliver both high security AND low friction.
But here's the challenge: even the best technology fails if the messaging doesn't match the user's mental model.Push a "frictionless" update to someone who deeply values control, and they might actually trust your product less.
The Missing Layer: Who's Behind the Screen?
This is where the breakthrough happens. By layering the OCEAN (Big Five) Personality traits with Schwartz's Theory of Basic Human Values, we can move from guessing to knowing - transforming security messaging from a one-size-fits-all broadcast into a precision instrument.
The OCEAN Framework: How People Behave
The Big Five personality model didn't emerge from a single eureka moment. It grew from decades of scientific investigation that began in the 1930s when psychologists Gordon Allport and Henry Odbert combed through Webster's Dictionary, extracting 18,000 words that described personality. They condensed this to 4,500 observable behavioral markers-a massive undertaking that revealed something remarkable: personality traits cluster into predictable patterns.
By the 1940s, researchers like D.W. Fiske began reducing these thousands of descriptors down to core dimensions. The real breakthrough came in the 1980s when Paul Costa and Robert McCrae of the National Institutes of Health developed the NEO Personality Inventory, which crystallized what we now know as the Big Five: Openness, Conscientiousness, Extraversion, Agreeableness, and Neuroticism-conveniently remembered by the acronym OCEAN.
What makes this model powerful for product design is its empirical foundation. The five-factor model has been validated across observers and cultures, making it one of the most robust personality frameworks in psychology. Unlike older theories that relied on clinical observation or philosophical speculation, the Big Five emerged from analyzing the actual language people use to describe themselves and others.
The Big Five personality dimensions describe how people naturally behave:
Openness to Experience
- Characteristics: Curious, inventive, willing to try new things
- Security behavior: These users are 63% more likely to adopt innovative, AI-enhanced passwordless features
- Messaging hook: "The future of secure login" / "Revolutionary protection"
- What works: Emphasize innovation, cutting-edge technology, being first
Conscientiousness
- Characteristics: Organized, dependable, detail-oriented
- Security behavior: High conscientiousness is negatively associated with compulsive or impulsive behaviors; these users plan before acting
- Messaging hook: "Complete control" / "Reliable protection"
- What works: Emphasize stability, manual control options, comprehensive features
Extraversion
- Characteristics: Energetic, social, seeking stimulation
- Security behavior: High extraversion intensifies reactions to service quality; these users respond to social proof
- Messaging hook: "Join millions who trust..." / "Award-winning security"
- What works: Social validation, community features, gamification
Agreeableness
- Characteristics: Compassionate, cooperative, trusting
- Security behavior: High agreeableness mitigates negative reactions to service issues; brand reputation matters more than specs
- Messaging hook: "Trusted by..." / "We protect what matters to you"
- What works: Emphasize trust, care, brand heritage
Neuroticism
- Characteristics: Prone to stress, anxiety-sensitive
- Security behavior: High neuroticism intensifies concerns about inadequate service; these users need constant reassurance
- Messaging hook: "You are safe" / "Always protected"
- What works: Stability, visible security indicators, proactive notifications
Recent research confirms these patterns hold across contexts. Personality influences consumer behavior, directly affecting interests, preferences, needs, and motivations, which in turn shape purchase decisions.
Schwartz's Values: Why People Care
While OCEAN describes how people behave, Schwartz's Theory of Basic Human Values describes why they care.
Developed by social psychologist Shalom H. Schwartz beginning in the early 1990s, this theory emerged from a fundamentally different question than the Big Five. Where personality psychology asked "how do people differ in their behavior patterns?", Schwartz asked "what motivates human action across all cultures?"
Drawing on earlier work by Milton Rokeach, Schwartz conducted research across 82 countries to identify universal human motivations. The theory identifies ten motivationally distinct types of values and specifies the dynamic relations among them; some values conflict with one another (like benevolence and power), whereas others are compatible (like conformity and security).
What makes Schwartz's framework particularly powerful is its circular structure. Values form a circular continuum where adjacent values are related to compatible motivations, while opposing ones are related to conflicting motivations. This isn't just elegant theory; this circular structure has been validated across culturally diverse groups, suggesting a universal organization of human motivations.
Schwartz identified ten universal values organized into four higher-order dimensions, but for security messaging, two are critical:
Conservation (Security, Conformity, Tradition)
- Core motivation: Safety, stability, preserving social order
- Security framing: Protection as a fundamental right
- Messaging angle: "Bank-grade protection" / "The security you can trust"
- Values that emphasize preserving existing social arrangements that give certainty to life
Openness to Change (Self-Direction, Stimulation, Hedonism)
- Core motivation: Autonomy, novelty, freedom of movement
- Security framing: Freedom enabled by security
- Messaging angle: "Seamless access" / "Security that gets out of your way"
- Values emphasizing independent thought and action - choosing, creating, exploring
Research shows that societies with higher economic performance often exhibit Openness to Change (valuing stimulation and self-direction), whereas more conservative markets prioritize Security and Tradition.
This isn't just academic theory. Recent studies show that values can influence audience responses to advertising appeals, and people tend to choose options that align more closely with their own values. In marketing research, moral values have proven to be one of the most powerful explanations of consumer behavior.
The 2026 Authentication Revolution: What's Actually Working
Before we dig deeper into the messaging framework, let's look at what's happening in the market - because these adoption patterns reveal user psychology in action.
Passkey authentications have more than doubled in a year, reaching 1.3 million per month, with 40% of users now storing at least one passkey. But the distribution is revealing:
E-commerce leads adoption: Retail accounts for nearly half of all passkey authentications, with Amazon alone representing 39.9%. Why? These platforms framed passwordless as friction reduction (Openness to Change), not security theater.
- Finance goes mandatory: Cryptocurrency exchange Gemini began requiring all users to create a passkey before accessing accounts in May 2025, producing a 269% rise in authentications. Why? Financial users value Conservation - they want protection, not convenience.
- Consumer tech sets defaults: Google's decision to make passkeys the default login for personal accounts exposed hundreds of millions of users to passwordless sign-ins, driving 352% growth in authentications.
The lesson? When given a choice between passwords and passkeys, adoption stalls. When companies match the messaging to the user's values and make the right choice default, adoption soars.
Building Your Messaging Framework: From Theory to Conversion
Here's how to transform these insights into a conversion engine:
Step 1: Diagnose Your Default Tilt
Audit your current messaging. Count statements in your onboarding flow that signal safety/stability versus ease/speed.
Security-first signals:
- "Protected" / "Verified" / "Secure" / "Bank-grade"
- Visual: Shields, locks, fortresses
- Colors: Blue, gray (trust, stability)
Convenience-first signals:
- "Instant" / "Seamless" / "Effortless" / "One-tap"
- Visual: Smooth flows, minimal elements
- Colors: Bright, energetic (speed, freedom)
If your user base scores high in Neuroticism but your copy is all about "Disrupting the industry," you have a messaging mismatch. Understanding the fundamental drivers of consumer behavior helps companies identify their target market and develop more effective marketing strategies.
Step 2: Define Target Profiles
Use psychographic segmentation to identify if your power users are "Security-seeking Traditionalists" or "Novelty-seeking Innovators."
Here's where the game has fundamentally changed. Traditional methods like the Schwartz Value Survey or Portrait Values Questionnaire still exist, but in 2025, AI can now automatically infer personality traits and values from how people actually speak and write and can help and provide answers to the most pressing questions like:
- Do users enable all optional security features? → High Conservation
- Do they adopt new features within days of launch? → High Openness
- Do they contact support frequently with security concerns? → High Neuroticism
- Do they have dozens of apps with saved logins? → High Convenience-seeking
Step 3: The 2.2 Messaging Matrix
Now comes the synthesis. We've established that personality (OCEAN) describes how people behave, and values (Schwartz) describe why they care. The messaging matrix combines these two dimensions to create four distinct psychological profiles-each requiring fundamentally different communication strategies.
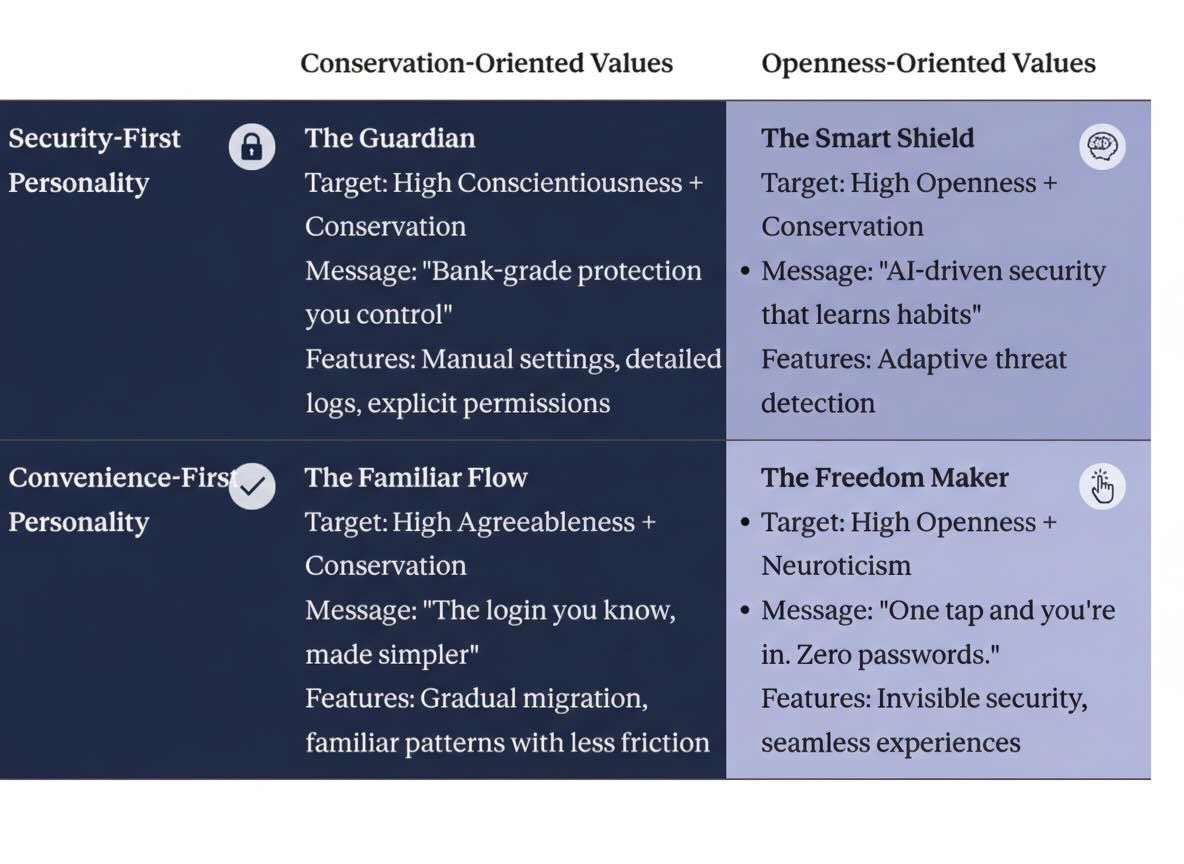
The Logic Behind the Matrix
The vertical axis represents personality orientation toward security-whether someone's natural behavioral tendency is to seek control and protection (high Conscientiousness, high Neuroticism) or to prioritize speed and ease (low Neuroticism, high preference for convenience).
The horizontal axis represents value orientation-whether someone's deeper motivations align with Conservation (security, tradition, stability) or Openness to Change (self-direction, stimulation, autonomy).
Here's why this matters: Someone can value security as a principle (Conservation) while preferring convenient implementations (Convenience-First personality). Think of the executive who demands enterprise-grade encryption but wants it to "just work" invisibly. Conversely, someone can have a Security-First personality (they actively manage settings) while valuing innovation and self-direction (Openness).
The four quadrants aren't just customer segments-they're distinct psychological worlds. Each requires messaging that addresses both their behavioral tendencies and their underlying values. Get this alignment right, and your features feel intuitive. Get it wrong, and even the best technology feels threatening or inadequate.
Step 4: Create and Test Variants
Here's where most companies waste money. Traditional A/B testing requires building multiple versions, splitting traffic, waiting for statistical significance, and hoping you tested the right variables. The average A/B test costs between $20,000-$50,000 when you factor in design, development, lost opportunity cost, and analysis time.
The breakthrough of 2025 isn't just detecting personality from language-it's using AI to create digital twins of your customer segments that you can interview, survey, and test against before writing a single line of production code. This means, within the digital twin you can predict the outcome of the different variants without burning cash.
Variant A (Guardian):
- Headline: "Your account is protected by military-grade encryption"
- Subhead: "You control every security setting"
- CTA: "Set up secure access"
- Visual: Strong, stable, controlled
Variant B (Freedom Maker):
- Headline: "Log in instantly. No passwords to remember."
- Subhead: "Secure by default. Simple by design."
- CTA: "Enable quick sign-in"
- Visual: Smooth, effortless, flowing
Research in psychological targeting shows that when targeting viewers based on personality traits like extraversion versus introversion, conversion rates double.
Real-World Application: What the Data Actually Shows
The effectiveness of psychologically-informed messaging isn't theoretical-it's measurable across the financial services industry.
The Baseline Reality
Approximately 64% of global financial institutions have deployed at least one form of biometric authentication, yet adoption rates among end users are more complex. Banks experienced an average 66% reduction in account takeover fraud within 12 months of implementing multi-modal biometric authentication systems, but getting users to actually enable these features has been the persistent challenge.
The Traditional Approach (One-Size-Fits-All)
When financial institutions launch biometric features with generic messaging like "Biometric security for instant access," they encounter predictable friction:
- Support tickets spike from users confused about privacy implications
- Adoption plateaus around 40-50% despite the feature being available
- Different user segments show wildly different adoption patterns that go unexplained
The problem? Generic financial advertising often fails because it doesn't address individual motivations.
The Psychographic Segmentation Advantage
Financial institutions using psychographic segmentation report stronger emotional connections with customers, relationships that translate into higher lifetime value and increased referral rates. Here's how it manifests in practice:
Example: DBS Bank Singapore
DBS Bank implemented an iris scanning authentication system at its ATMs, with transaction times decreasing by 42% while customer satisfaction scores increased by 31%. But their success came from segmented rollout messaging:
- For Security-First users: Emphasized the uniqueness of iris patterns and impossibility of replication
- For Convenience-First users: Highlighted the elimination of card loss risk and faster transactions
Example: Bank of America
Bank of America's mobile banking app integrates multiple biometric authentication options, resulting in a 52% reduction in fraud incidents and a 23% increase in mobile banking engagement. Their strategy included offering choice-recognizing that some personality types need control while others want default simplicity.
The Conversion Impact
Research across financial services demonstrates the power of psychographic alignment:
- 76% of consumers are more likely to buy from brands that personalize their messaging, and 71% simply expect personalized communication
- Campaign personalization based on psychological profiles generates measurably better results than broad demographic targeting
- Security-focused customers respond to stability messaging, while growth-oriented customers prefer opportunity-focused campaigns
The Cultural Context Variable
Messaging that works in a "Security-first" market, such as Germany may fail in a "Convenience-first" market, such as the US. But it's more nuanced than that.
In June 2025, the UAE Central Bank required all licensed financial institutions to eliminate SMS and email OTPs by March 2026. This regulatory push reflects cultural values: in markets with high Conservation orientation, mandatory security upgrades are accepted. Try the same in high-Openness markets, and you'll face backlash.
The solution isn't to pick one approach. It's to segment within markets:
- Germany: Even Openness-oriented users want control - frame innovation as "giving you options"
- US: Even Conservation-oriented users expect speed - frame security as "invisible protection"
- Singapore: High-tech + high-trust - combine innovation with authority messaging
Beyond Authentication: The Broader Implications
This framework extends far beyond login screens. Every digital interaction involves a security-convenience trade-off:
Data Sharing
- Conservation + Conscientiousness: "You decide exactly what data we collect"
- Openness + Extraversion: "Smart features that learn from your preferences"
Privacy Settings
- High Neuroticism: "Review your privacy choices anytime. We'll notify you of any changes."
- Low Neuroticism + High Openness: "Optimized for you. Adjust if you want."
Feature Adoption
- Agreeableness: "Join the community of 50M users who trust..."
- Openness: "Be among the first to experience..."
A 2025 study of e-commerce users found that individuals high in Agreeableness tend to follow trends endorsed by influencers they trust, while those high in Conscientiousness usually budget before shopping and avoid impulsive purchases.
Measuring Success: Beyond Conversion Rates
Track these metrics to validate your framework:
Adoption Metrics
- Feature activation rates by segment
- Time-to-first-use by personality cluster
- Long-term retention (not just initial conversion)
Support Metrics
- Support ticket volume by segment
- Sentiment analysis of user feedback
- Time-to-resolution by concern type
Behavioral Signals
- Settings customization frequency (Conservation indicator)
- New feature exploration (Openness indicator)
- Security notification engagement (Neuroticism indicator)
In 2025, 7% of users did not use a password for any sign-ins, validating that enterprise-scale password elimination is achievable today. Your goal isn't to convert everyone immediately - it's to optimize messaging for each segment's natural adoption curve.
The Technology-Psychology Synthesis
Here's what the data makes clear: The old argument that robust security must come at the expense of user productivity is not supported by the data. Following Accenture's introduction of passwordless authentication, phishing attacks declined by 60%.
The technology works. 100% of businesses that adopted FIDO standards have seen significant improvements in security and user experiences, along with a reduction in help desk and support issues. But technology alone isn't enough. Advanced methods like FIDO2 and Passkeys actually improve both security and UX, but you must frame them correctly to get adoption.
This is where personality psychology becomes your competitive advantage. While your competitors are arguing about feature sets, you're speaking directly to user motivations.
The Bottom Line
The passwordless authentication market is projected to reach $55.7 billion by 2030, growing at 18.24% CAGR. Companies that understand the psychology behind adoption will capture disproportionate value.
But this isn't really about authentication. It's about understanding that every product decision involves competing values. Every feature you ship makes a promise about what your users should care about.
The question isn't whether to prioritize security or convenience. The question is: for which users does security feel like freedom, and for which users does convenience feel like risk?
Answer that, and you're no longer guessing. You're engineering conversion through psychology.
